Project Description

Introduction:
In the last two decades, the number of Internet users worldwide has been increasing non-stop. The quickly evolving IT industry has seen many breakthrough innovations that have completely changed the way we communicate and do business, specially in the last decade, with the appearance of mobile technology, which made possible to reach and connect to the Internet everywhere.
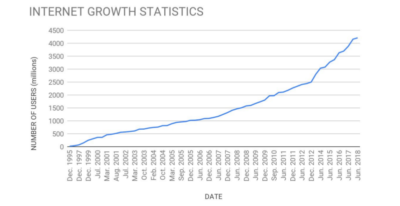
This increase has had a direct impact on the workload web applications, services, and, therefore, servers have to handle and serve. On the other hand, an increasing number of
internet users also mean a larger pool of potential security attacks victims. In 2018, according to IBM , “The average data breach takes 196 days to detect and costs the company 3.9 Million USD”.
To handle the increased workload, the industry has been forced to evolve, innovate, and find new ways to satisfy the users’ needs and demands. The appearance of Cloud Computing has been able to provide an effective answer to the increasing and varying capacity problems.
Thanks to virtualization technologies, cloud providers are able to offer configurable computer system resources on customer demand. More recently, with the appearance of
containers, a newer virtualization technology, this task has become even more efficient. One of the most well-known container companies is Docker, which describes containers as “a standard unit of software that packages up code and all its dependencies so the application runs quickly and reliably from one computing environment to another”.
According to Datadog, a modern monitoring and analytics platform provider, “At the beginning of April 2018, 23.4 percent of Datadog customers had adopted Docker, up from 20.3 percent one year earlier. Since 2015, the share of customers running Docker has grown at a rate of about 3 to 5 points per year”. Looking at the data, the trend clearly shows an increasing use of the containerization technology.
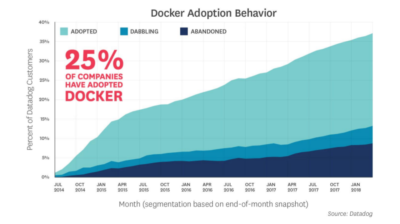
While it’s undeniable that containerization has provided a more efficient way to handle the capacity problems, it also introduces new challenges. Providing secure and malware-free web services that are running on thousands of containers is one of them.
Business model:
Kontained is a project whose purpose is to address this challenge by developing a real-time monitoring and analysis tool that leverages machine learning to recognize containers’
exceptional events for Cloud Service Providers and Private Cloud Operators companies, who lack modern, effective and competent security services and tools for the analysis of its containers’ behavior.
With Kontained, we want our customers to increase their confidence in their cloud platforms, deployed with containerization technologies, and reduce the cost of their security
infrastructure. It’s very difficult to quantify what’s the exact value for each company, since the consequences and impact malicious attacks and data breaches highly varies depending on the company size and type, and the attack itself, its degree of success, damage dealt or stolen data.
We could make a simple and superficial approximation of the value for our customers by following the 2017 State of Cybersecurity in Small & Medium-sized Businesses report’s numbers. According to this study, “ 55 percent of respondents say their companies have experienced a cyber attack in the past 12 months (May 2015 -May 2016) ” . Also, “ In 2017, average malware-related costs for small and medium-sized businesses included $1,027,053 due to damage or theft of IT assets, and $1,207,965 due to disruption to normal business operations ” . We could calculate an approximate customer value by performing simple math operations and assuming a proporcionality. Based on the costs and attack percentage, the average cost of security attacks would be $1,229,259.9. From this, we would need to discard those attacks that, because of its nature, Kontained can’t detect, such as social engineering, stolen devices, and so on. The yearly cost of attacks that Kontained could detect decreases to $704,857.63. Now, assuming Kontained is able to keep up to the expectations and detect, at least, up to 80% of the attacks, it would save the customer up to $563,886.10.
But, what the customers gain is not only a save in costs, according to the U.S. National Cyber Security Alliance, 60% of small companies are unable to sustain their business more than six months following a cyberattack. Kontained customers will also see the chances of being forced to discontinue its business after a cyberattack lowered.
We made several assumptions we would need to validate to start working and shaping the idea and the business model behind it: companies are not aware enough of the security risks, they lack effective but security systems to prevent breaches and malicious attacks, they use containerization technologies for their deployments, operation teams have to deal with securitization of their deployments with inefficient tools and processes, and that the best pricing strategy for a software solution is a subscription based model for customers.
After our first round of interviews we could validate some of our assumptions and adapt there where we were wrong. We learnt that companies are, in fact, aware of security risks, they’re willing to invest in effective solutions and they already have security systems and tools among several layers to reduce the probability of successful malicious attacks. Operation teams are actually not overwhelmed by security concerns, by the time the application has to be deployed it has already passed several security filters and should be somewhat secure. Finally, while the subscription model wasn’t the favorite one for one of the interviewees, we still believed it would help us scale for a huge number of customers.
In summary, we ended up with a product for all kind of companies, that would use containerization technologies, who were in need of a security solution for its container
deployments, paid as a subscription service.
As we kept developing the business model, we started seeing the flaws and the potential points of failure of such business model. Our customer segment was too broad and fuzzy, we weren’t targeting specific companies nor the concrete persons that would actually pay for our product. There weren’t clear and concrete objectives. Our competitive advantage wasn’t clear enough. And, finally, we didn’t work on the value of our solution neither the perceived value by our customers.
The first issue we wanted to address was the broad target market we were aiming at. We moved from targeting all companies that would use containers to focus only on developing the product and aim for an acquisition from a big Cloud Provider. By doing so, our solution would reach millions of users instantly. However, after thinking about this approach, studying its viability and how do technological acquisitions actually work, we had to scrap the idea.
The only way to be acquired is to bring attention, raise interest, and have something the buyer wants: talent, property or products, processes, or an innovative business model. And the only way to raise interest is to have a successful and sustainable business model, which we completely lacked.
From there, we redesigned the business model once again, the customer segments, and the main activities we would carry out.
First, we decided to focus on medium sized (more than 50 employees and less than 250) Private Cloud Operators and Public Cloud Providers companies with hopes to reach bigger companies as the project grows.
The thinking behind the size limitation is because, as we learnt from from our interviews, medium and big companies tend to invest more resources into security than small companies and big companies can be hard to reach at the beginning. We put a special eye on small companies who are steadily growing and will become medium sized companies in a short span of time that are starting to look for their first security solutions for their application deployments.
On the other hand, we decided to focus on these two types of companies since they are potential doors to the millions of containers that their customers or users run on their clouds. With this approach we can still leverage the scalability and reach of our solution but focusing fewer customers directly.
Within these companies, and depending on the company characteristics, activities, maturity, and size, we have identified the roles we should aim to contact and sell our product to: Cyber Security Consultants, Security Analysts, Dev(Sec)Ops Engineers, and companies’ CTO.
Second, we expanded our activities beyond the development and maintenance of the product and the customer support service. We further developed the idea of the customer
support. Since we are targeting and much more small but concrete customer segment, we can have two separate integration teams.
Each team would integrate Kontained either in a Private Cloud Operator cloud or in a Public Cloud Provider cloud. The main goal of these two teams is to guarantee that our customers integrate our solution correctly and make the most out of it.
The main revenue stream will be our customers, who will have to pay for our product and its integration in their cloud. Similarly to our initial subscription based approach, we propose a pay-per-use pricing that will be further explained in the pricing strategy section.
Apart from the main customer segment that has been described, we also welcome and count on security researchers and software developers to collaborate, test, and improve the
product in exchange for a cheaper and more affordable access to the technology. By doing this, we will be able to, not only increase the product’s quality, effectivity, and usefulness but also, build a network that will continuously nourish the project with experience and knowledge, serve as a solid foundation for the company growth, and work as a convincing factor when negotiating with potential customers or developing an actually realistic exit strategy.
Additionally, we believe we are on an advantageous position. As Master students, we are close to research centers and state-of-the-art security research while, at the same time, we have the EIT Digital business resources to bring Kontained’s innovative integration to market faster than the competition.
Still, we are aware of the important effort we will have to make in order to gain visibility and trust from other companies. We plan to attend to IT events and conferences such as AWS re:Inforce Conference , RSA Conference , or DockerCon to expand our network and TNW Conference , 4 Years From Now , or Seed Start Summit to increase our startup visibility. As a complementary activity, but still to increase visibility and trust, we want to publish cloud and security related articles in our website and publish research related white papers.
To finish with, we have defined some metrics or that can help us track our progress: number of collaboration partnerships, number of customers, number of cloud integrations, number of containers monitored per customer, and blog articles readings/subscriptions, to begin with.
Team:
Luc Powell
Stephan Hauser
Pierrick Philippe
Daniel Funke
Lyu Tuojian